ParaSpace contest - Englave's results
The First Ever Cross-Margin NFT Financialization Protocol.
General Information
Platform: Code4rena
Start Date: 28/11/2022
Pot Size: $192,500 USDC
Total HM: 33
Participants: 106
Period: 11 days
Judge: LSDan
Total Solo HM: 15
Id: 186
League: ETH
Findings Distribution
Researcher Performance
Rank: 39/106
Findings: 1
Award: $372.29
🌟 Selected for report: 1
🚀 Solo Findings: 0
Findings Information
🌟 Selected for report: Englave
Also found by: 9svR6w, Jeiwan, Josiah, Lambda, RaymondFam, Trust, csanuragjain, kaliberpoziomka8552, minhquanym, unforgiven
Labels
Awards
372.2896 USDC - $372.29
External Links
Lines of code
Vulnerability details
Impact
During _removeFeeder operation in NFTFloorOracle contract, the feeder is removed from feeders array, and linking in feederPositionMap for the specific feeder is removed. Deletion logic is implemented in "Swap + Pop" way, so indexes changes, but existing code doesn't update indexes in feederPositionMap after feeder removal, which causes the issue of Denial of Service for further removals.
As a result:
- Impossible to remove some
feedersfrom the contract due to Out of Bounds array access. Removal fails because of transaction revert. - Data in
feederPositionMapis corrupted after somefeedersremoval. Data linking fromfeederPositionMap.indextofeedersarray is broken.
Proof of Concept
address internal feederA = 0x5B38Da6a701c568545dCfcB03FcB875f56beddC4; address internal feederB = 0xAb8483F64d9C6d1EcF9b849Ae677dD3315835cb2; address internal feederC = 0x4B20993Bc481177ec7E8f571ceCaE8A9e22C02db; function corruptFeedersMapping() external { console.log("Starting from empty feeders array. Array size: %s", feeders.length); address[] memory initialFeeders = new address[](3); initialFeeders[0] = feederA; initialFeeders[1] = feederB; initialFeeders[2] = feederC; this.addFeeders(initialFeeders); console.log("Feeders array: [%s, %s, %s]", initialFeeders[0], initialFeeders[1], initialFeeders[2]); console.log("Remove feeder B"); this.removeFeeder(feederB); console.log("feederPositionMap[A] = %s, feederPositionMap[C] = %s", feederPositionMap[feederA].index, feederPositionMap[feederC].index); console.log("Mapping for Feeder C store index 2, which was not updated after removal of B. Feeders array length is : %s", feeders.length); console.log("Try remove Feeder C. Transaction will be reverted because of access out of bounds of array. Data is corrupted"); this.removeFeeder(feederC); }
Snippet execution result:
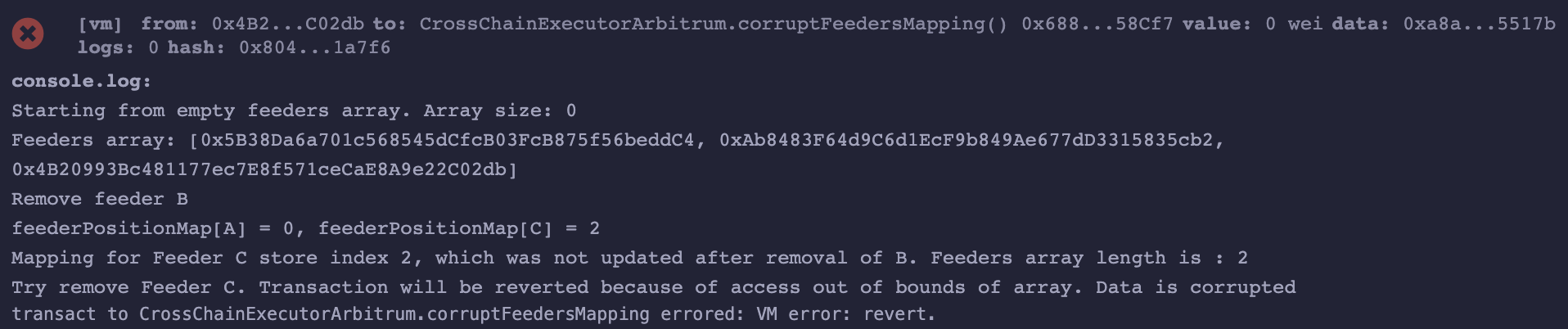
Tools Used
Visual inspection; Solidity snippet for PoC
Recommended Mitigation Steps
Update index in feederPositionMap after feeders swap and pop.
feeders[feederIndex] = feeders[feeders.length - 1]; feederPositionMap[feeders[feederIndex]].index = feederIndex; //Index update added as a recommendation feeders.pop();
#0 - c4-sponsor
2022-12-06T03:54:32Z
yubo-ruan marked the issue as sponsor confirmed
#1 - c4-judge
2022-12-20T17:36:16Z
dmvt marked the issue as duplicate of #47
#2 - c4-judge
2022-12-20T17:38:41Z
dmvt marked the issue as duplicate of #47
#3 - c4-judge
2022-12-20T17:40:53Z
dmvt marked the issue as selected for report
#4 - c4-judge
2023-01-23T15:47:34Z
dmvt marked the issue as satisfactory
#5 - trust1995
2023-01-23T15:55:43Z
I've submitted this report as well. However, I believe it does not meet the high criteria set for HIGH severity finding. For HIGH, warden must show a direct loss of funds or damage to the protocol that stems from the specific issue. Here, there are clearly several conditionals that must occur in order for actual damage to take place. Regardless, will respect judge's views on the matter
#6 - dmvt
2023-01-27T09:54:10Z
I've submitted this report as well. However, I believe it does not meet the high criteria set for HIGH severity finding. For HIGH, warden must show a direct loss of funds or damage to the protocol that stems from the specific issue. Here, there are clearly several conditionals that must occur in order for actual damage to take place. Regardless, will respect judge's views on the matter
I respectfully disagree. The scenario is likely to occur at some point during normal operation of the protocol. The inability to remove dead or malfunctioning feeders can easily lead to the complete breakdown of the protocol and significant funds loss, the "data corruption" mentioned in the report. The severity of this issue, when it occurs, justifies the high risk rating.
#7 - C4-Staff
2023-02-01T19:09:50Z
captainmangoC4 marked the issue as selected for report